Mastering Security Information And Event Management (SIEM): Implementation Guide For Your EBook
In today's digital age, security information and event management (SIEM) implementation has become a cornerstone for safeguarding organizational data and ensuring robust cybersecurity measures. With cyber threats evolving at an alarming rate, businesses are increasingly turning to SIEM solutions to monitor, analyze, and respond to security incidents in real-time. This comprehensive guide delves into the intricacies of SIEM implementation, offering actionable insights for organizations looking to enhance their security posture.
As we navigate through this detailed exploration of SIEM implementation, you will gain a deep understanding of its importance, the key components involved, and how it can be effectively integrated into your existing IT infrastructure. Whether you're a cybersecurity professional or a business leader, this guide aims to equip you with the knowledge needed to make informed decisions about your organization's security strategy.
This article is tailored to provide practical advice and expert insights, ensuring that you can leverage SIEM technology to protect your organization's digital assets effectively. By the end of this guide, you will have a clear roadmap for implementing SIEM solutions and maximizing their potential for safeguarding your business.
Read also:William Zabkas Children Uncovering Their Ages And Family Life
Table of Contents
- Introduction to SIEM
- Key Components of SIEM
- Benefits of SIEM Implementation
- The SIEM Implementation Process
- Choosing the Right SIEM Solution
- Cost Considerations for SIEM
- Common Challenges in SIEM Implementation
- Best Practices for SIEM Deployment
- Integrating SIEM with Other Security Tools
- The Future of SIEM
Introduction to Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) is a technology designed to provide comprehensive security monitoring and incident response capabilities. SIEM systems aggregate and analyze data from various sources within an organization's IT infrastructure, offering real-time insights into potential security threats. The primary goal of SIEM is to detect and respond to security incidents swiftly, ensuring that organizations can mitigate risks and protect sensitive data.
SIEM solutions combine security information management (SIM) and security event management (SEM) functionalities, enabling organizations to monitor security events in real-time while also storing and analyzing historical data for compliance and forensic purposes. This dual functionality makes SIEM an essential tool for modern cybersecurity strategies.
The Evolution of SIEM Technology
SIEM technology has evolved significantly over the years, adapting to the changing landscape of cyber threats. Initially, SIEM systems focused primarily on log management and basic event correlation. However, advancements in artificial intelligence (AI) and machine learning (ML) have enhanced their capabilities, allowing for more sophisticated threat detection and predictive analytics.
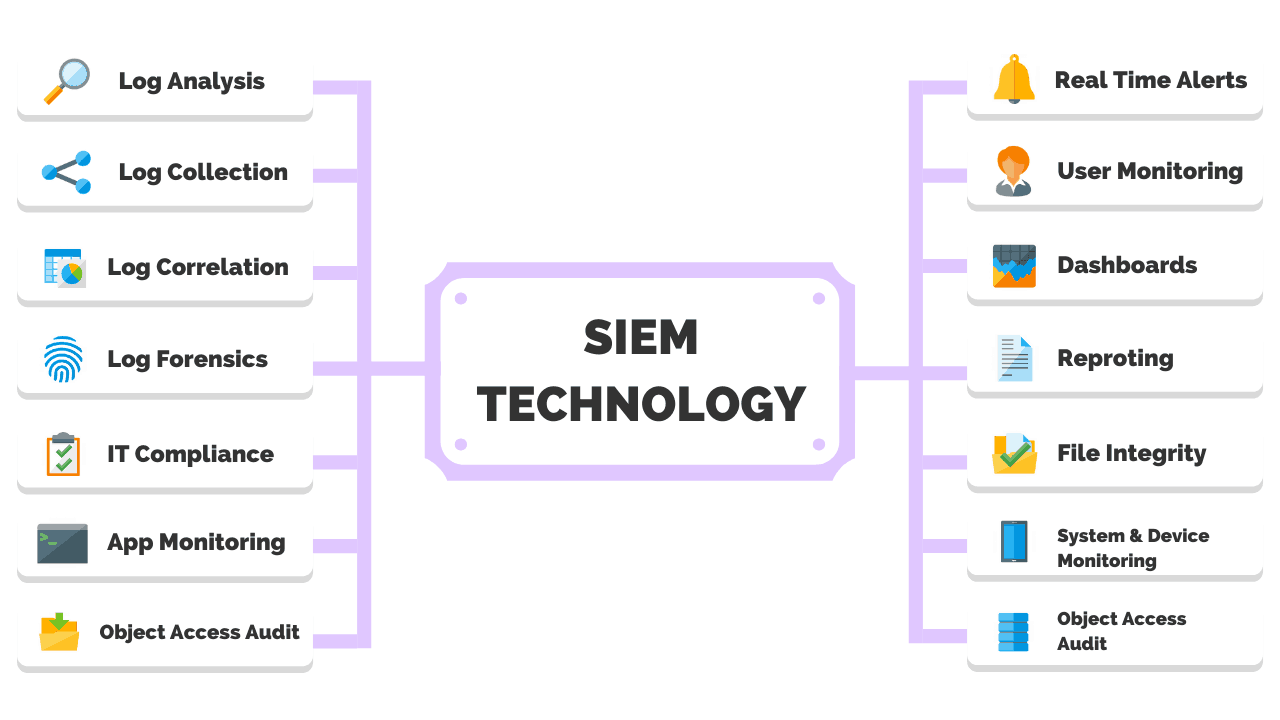
Key Components of SIEM Systems
Understanding the key components of SIEM systems is crucial for successful implementation. These components work together to provide a holistic view of an organization's security posture. Below are the essential elements:
- Data Collection: Gathering logs and events from various sources across the network.
- Data Normalization: Standardizing data formats for consistent analysis.
- Correlation Engine: Identifying patterns and relationships between events to detect potential threats.
- Alerting and Notification: Generating alerts for suspicious activities and notifying security teams.
- Reporting and Compliance: Generating reports for regulatory compliance and auditing purposes.
Data Sources for SIEM Systems
SIEM systems rely on data from multiple sources to provide comprehensive monitoring. These sources include:
- Firewalls
- Intrusion Detection Systems (IDS)
- Antivirus Software
- Network Devices
- Application Logs
Benefits of SIEM Implementation
The implementation of SIEM solutions offers numerous benefits for organizations seeking to enhance their cybersecurity measures. Some of the key advantages include:
Read also:Bradley Cadenhead The Journey Of A Remarkable Entrepreneur
- Real-Time Threat Detection: SIEM systems provide continuous monitoring and immediate alerts for potential security incidents.
- Compliance Management: SIEM solutions help organizations meet regulatory requirements by generating detailed reports and maintaining audit trails.
- Incident Response: With SIEM, security teams can respond to incidents more efficiently, reducing the time it takes to contain and mitigate threats.
- Cost Savings: By preventing security breaches and minimizing downtime, SIEM implementation can lead to significant cost savings for businesses.
Return on Investment (ROI) of SIEM
Investing in SIEM technology can yield substantial returns in terms of improved security and operational efficiency. Studies have shown that organizations implementing SIEM solutions experience fewer security breaches and reduced downtime, translating into tangible cost savings and enhanced reputation.
The SIEM Implementation Process
Successfully implementing a SIEM solution requires a structured approach. Below is a step-by-step guide to help you navigate the implementation process:
- Assess Your Security Needs: Identify the specific security challenges your organization faces and determine how SIEM can address them.
- Select Data Sources: Determine which data sources to include in your SIEM system for comprehensive monitoring.
- Deploy the SIEM Solution: Install and configure the SIEM software, ensuring it integrates seamlessly with your existing IT infrastructure.
- Test and Optimize: Conduct thorough testing to ensure the SIEM system functions as intended and optimize settings for maximum effectiveness.
Implementation Timeline
The timeline for SIEM implementation can vary depending on the complexity of your IT environment and the scope of the project. On average, organizations can expect the process to take several weeks to a few months.
Choosing the Right SIEM Solution
With numerous SIEM solutions available in the market, selecting the right one for your organization can be challenging. Consider the following factors when evaluating SIEM vendors:
- Scalability: Ensure the solution can grow with your organization's needs.
- Integration Capabilities: Choose a SIEM system that integrates well with your existing tools and technologies.
- Support and Training: Opt for vendors that offer robust support and training programs to ensure successful deployment.
Vendor Comparison
Comparing different SIEM vendors is essential to find the best fit for your organization. Some of the leading SIEM providers include Splunk, IBM QRadar, and Microsoft Sentinel. Each offers unique features and capabilities, so it's important to assess them based on your specific requirements.
Cost Considerations for SIEM
Implementing a SIEM solution involves various cost considerations. These include:
- Software Licensing Fees
- Hardware Costs
- Professional Services for Deployment and Configuration
- Ongoing Maintenance and Support
Budget Planning Tips
Effective budget planning is crucial for SIEM implementation. Start by estimating the total cost of ownership (TCO) over a three-to-five-year period and allocate resources accordingly. Additionally, consider potential cost savings from reduced security incidents and improved operational efficiency.
Common Challenges in SIEM Implementation
While SIEM solutions offer numerous benefits, their implementation can present challenges. Some common obstacles include:
- Data Overload: Managing the vast amount of data generated by SIEM systems can be overwhelming.
- False Positives: SIEM alerts may sometimes generate false positives, leading to unnecessary investigations.
- Resource Constraints: Limited personnel and expertise can hinder successful SIEM deployment.
Strategies for Overcoming Challenges
To address these challenges, organizations can adopt strategies such as implementing data filtering techniques, fine-tuning alert thresholds, and investing in staff training and development.
Best Practices for SIEM Deployment
To ensure successful SIEM deployment, follow these best practices:
- Define Clear Objectives: Establish specific goals for your SIEM implementation and align them with your overall security strategy.
- Involve Key Stakeholders: Engage relevant departments and personnel throughout the implementation process to ensure buy-in and support.
- Monitor and Evaluate: Continuously monitor the performance of your SIEM system and make adjustments as needed to optimize results.
Ongoing Management and Optimization
SIEM systems require ongoing management and optimization to remain effective. Regularly update rules and configurations to adapt to evolving threats and organizational changes.
Integrating SIEM with Other Security Tools
SIEM solutions are most effective when integrated with other security tools, such as endpoint detection and response (EDR), threat intelligence platforms, and identity and access management (IAM) systems. This integration enhances the overall security posture of an organization by providing a more comprehensive view of potential threats.
Benefits of Integration
Integrating SIEM with other security tools offers several advantages, including improved threat detection, streamlined incident response, and enhanced compliance management.
The Future of SIEM
The future of SIEM is promising, with advancements in AI and ML driving innovation in threat detection and response. As cyber threats continue to evolve, SIEM systems will become even more sophisticated, offering predictive analytics and automated response capabilities to help organizations stay ahead of potential attacks.
Emerging Trends in SIEM Technology
Some of the emerging trends in SIEM technology include cloud-based solutions, behavioral analytics, and integration with DevSecOps practices. These developments will further enhance the capabilities of SIEM systems and their role in modern cybersecurity strategies.
Conclusion
In conclusion, security information and event management (SIEM) implementation is a critical component of any organization's cybersecurity strategy. By understanding the key components, benefits, and challenges of SIEM systems, you can make informed decisions about their deployment and maximize their potential for safeguarding your business. We encourage you to share your thoughts and experiences with SIEM implementation in the comments section below. Additionally, explore other articles on our site for more insights into cybersecurity and IT management.